People are becoming more conscious of safeguarding their data from unnecessary online interuptions. Forbes reveal that 66% individuals use virtual private networks to protect their data from onine threats.
For businesses, they embrace proxy servers to act a link between their enterprises and the web. There are a lot of opportunities that comes with using these layers. This article will explore the fundamentals of proxy servers and how you can use them to your organization’s advantage.
What is a Proxy Server?
Simply put, a proxy server is a masking layer between a user and the world wide web. It acts as a protection and cloud network security wall that not only protects user data but also provides improved network performance.
Apart from offering privacy and protection, one of the most important features of a proxy server is that it can unblock blocked websites.
There are lot of points to consider when routing servers to and from destinations in a way that optimizes the network architecture, here are a few:
- Performance improvement on the network
- Improvement of Firewall or filter, data/information security
- The ability to cache data in a way that simplifies repetitive requests
- Provision of better privacy protection
- By routing requests for information through local IP addresses, the success rate of data collection can be increased
What Does A Proxy Server Do?
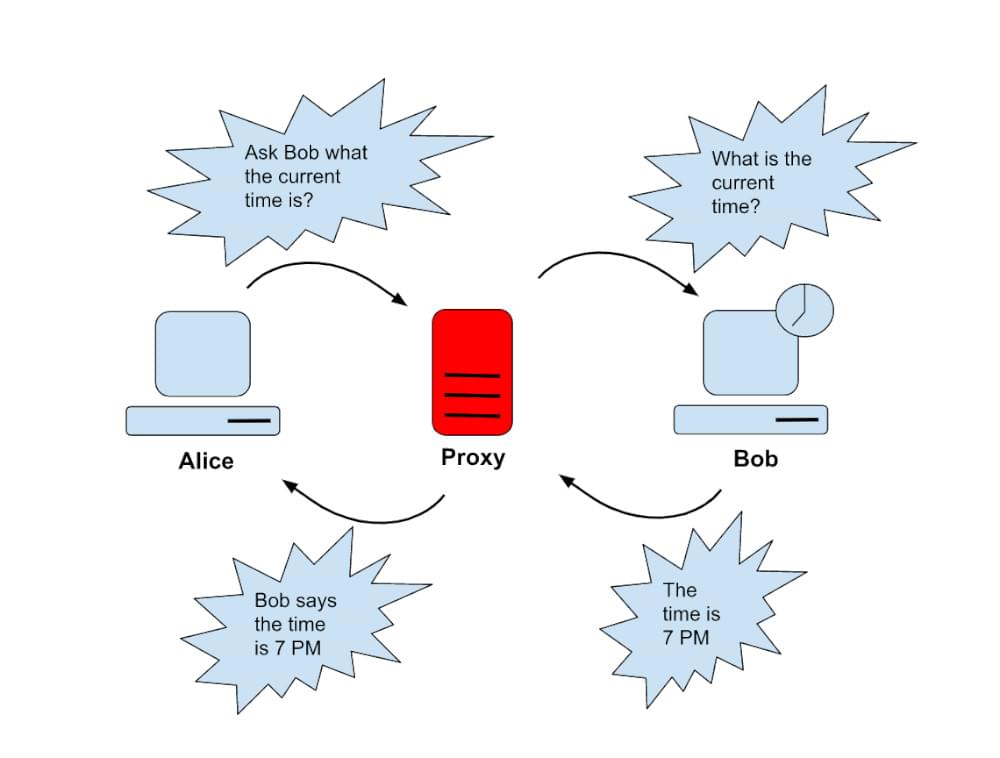
There is an IP address assigned to every computer. You can now communicate with other devices since they know who requests and receives information. However, individuals or businesses interested in using a proxy are doing so for a specific reason.
The proxy is introduced here as a third entity. It is similar to a computer is that proxies have their IP addresses the same way computers do. There is no interest on their part in direct communication. The proxies have several beneficial capabilities on top of this, including the following:
- Make sure your real IP address is not visible to other devices
- Traffic should be routed through other IP addresses to fool the target site into thinking that a local device is trying to access information on it
- It is advisable to encrypt information/data that you are interested in receiving or transmitting to prevent it from being intercepted by an undesirable third party
- For places of business or universities that want to maximize the use of computers for work instead of play, you can block access to certain websites for specific IP addresses
As a whole, various geolocation proxies act as an umbrella that helps shield your location and identity from the outside world while still allowing you to retrieve open source web data without being discriminated against based on your geolocation or any other factor.
How Does A Proxy Work?
An IP address is a unique identifier a computer uses to communicate with another node. When you send a web request, your request is sent to a proxy server first, which then routes it to the web server. Similarly, your computer knows the IP address of the proxy server that your proxy server is using.
As a proxy, it sends a request on your behalf to the internet and then collects the data from the internet and makes it available to you. Moreover, it is an excellent way to ensure that your data is not hacked. A proxy can change your IP address so that the web server will not be able to locate your location in the world. Furthermore, some web pages can also be blocked. Shared proxies operate differently. When it comes to shared proxy, they provide an optimal solution that balances cost and performance. These proxies can offer a combination of anonymous browsing, robust security, and fast internet access, making them well-suited for routine web scraping tasks. By sharing IP addresses among multiple users, the cost per user is reduced.
Why Should You Use A Proxy Server?
The data breach is a common issue these days where even the best organizations try to avoid it through strict data usage policies. Other than that, any online transaction, sensitive or private development, can be hidden behind a proxy so that there is an additional layer of security. Companies use these servers to limit their employees from accessing unsafe and non-relevant websites so that their ideas don’t get into the wrong hands.
You may want to promote your business through social media but can not do it normally with one IP Address without getting suspended or even blocked. So you have to rotate proxies to create multiple accounts on the internet.
Moreover, cloud storage services and cloud proxies are be used to speed-up internet networks by caching the files requested prior, peering web pages between ISP rather than the internet to save on bandwidth, filtering ads, and compressing web traffic to suffice the events of overload.
Organizations across different industries scrape all kinds of data to conduct market research on smaller websites, insensitive to scraping compared to the big ones. This is done through datacenter proxies.
Some companies may use datacenter proxy server as a cheap way to review negativity when it starts due to the web’s transparency. You can use proxies to cop on products across the globe. This works by constantly rotating proxies, getting as many proxies as accounts, and combine bots so that the websites do not realize where these hits are coming from.
According to a case study, a client had their scrapers blocked due to their proxy getting blocked by the search engine, and a large portion of their requests timed out as which might be due to datacenter proxies. But later used residential proxies and stopped facing these issues and even generated results up to 5 times faster and paid just 10 percent extra.
Those were some of the uses of a proxy server. There are several more, and you can even think of them in your own way.
Types of Proxies
Proxy servers are in high demand. Following are proxy usage statistics around the world!
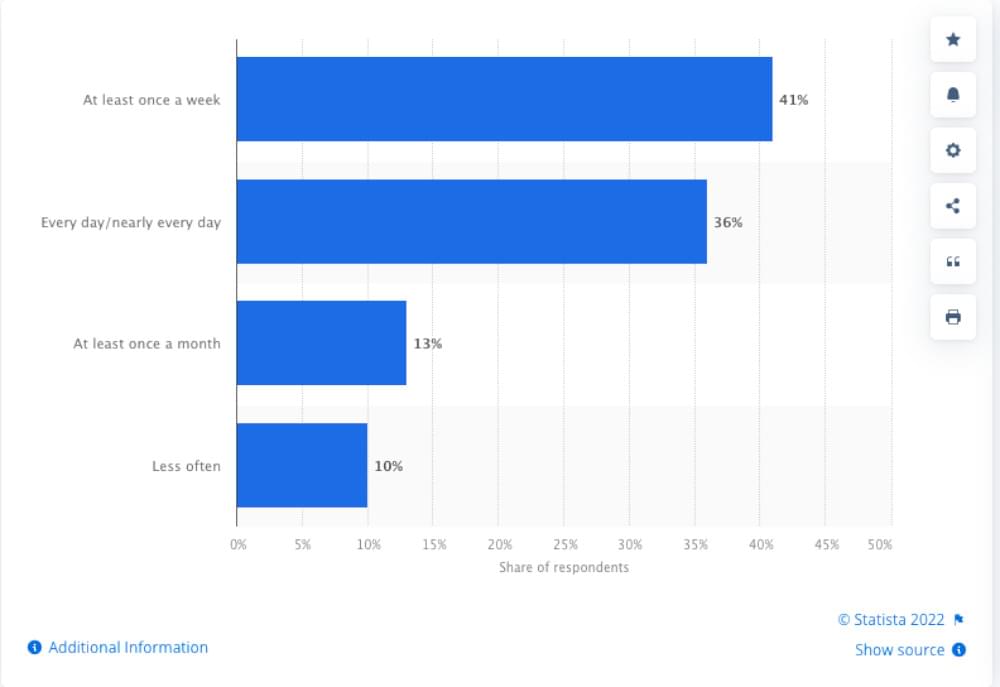
Such popularity calls for variety and extensive functionality. Therefore, proxies are currently available in wide different varieties, each offering unique capabilities and features in addition to their ability to act as a proxy server.
Whichever proxy type we take, the end idea is to help use maintain anonymity and safely surf through the world wide web. Some of the main types are as follows:
1. Data Center Proxy
In datacenter proxy server, a single server is typically assigned many IP addresses through which all traffic is routed. This type of proxy server is completely independent of your (ISP) or internet connection. A data center proxy hides your IP without getting linked to one place.
For use cases where data origin uniformity is integral, companies choose data center proxies for their speed and low operating costs.
The only problem with datacenter proxies is that websites can often detect them which results in the user getting flagged.
2. Residential Proxy
This type of proxy offer IP addresses connected to real residential address, which makes them impossible to ban. In addition to being used to collect data from sophisticated target sites, residential proxies can also be used to view information from the perspective of a real/local consumer, as well as handle an increased number of simultaneous data requests. Then there are others like internet service provider (ISP) proxy, mobile proxy, public proxy, and so on.
Related: Datacenter vs Residential Proxies
3. Mobile Proxies
Mobile proxies can specifically be set up using a 3G or 4G phone network. This type of proxy server operates as an intermediate internet connect using a third party service provider. Mobile proxies can only be used on smart phones or tablets as they require sim usage.
A mobile proxy makes use of IP addresses that are dynamically issued to mobile devices by their Mobile Network Operator (MNO), who also serves as their Internet Service Provider (ISP).
4. Socks5 Proxy
As of right now, roughly 66% of active proxies are marked as trustworthy, while around 24% are marked as unrated.
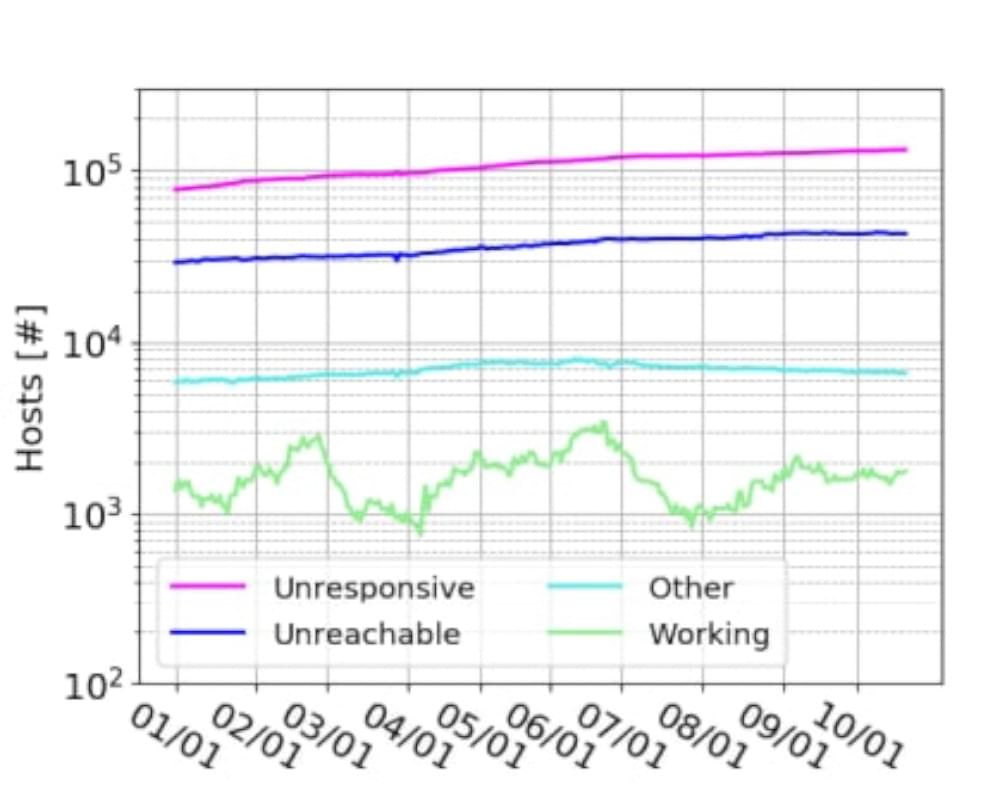
HTTPS is supported by only 17,350 proxies, which is only 40% of the total proxies. So what about the rest of the proxies? When comparing SOCKS proxy vs HTTP proxy, SOCKS5 proxy servers are more flexible and secure proxies designed to handle programs and protocols without any limitation. This type of proxy server creates path through network firewall.
SOCKS5 is the optimized version of SOCKS that routes web traffic through a remote server. The SOCKS5 proxy protocol provides advanced security via multiple authentication methods. This means that only authorized users will be able to connect to SOCKS5 proxy.
5. Reverse Proxy
Reverse proxies operates alternatively of how other proxies operate. These type of proxies routes traffic on behalf of multiple servers. Rather than offer an IP address to a location, it becomes a gateway between the user, client and internet
Here’s how it works: Reverse proxies receive client requests, forward them to another server, and return the results to the clients. Server performance, security, and reliability can all be enhanced with it.
Reverse proxy enables you to load balance traffic or improve performance by caching data from the destination server and sending it back to the reverse proxy server.
Example: One of the most useful security measures to protect the host’s true identity is to listen for TCP port 80 website connections, which are usually placed in the demilitarized zone (DMZ) zone where publicly accessible services are placed for public access.
Moreover, since external users cannot identify the number of internal servers, this method will be transparent to external users. Therefore, the reverse proxy’s primary duty is to redirect the flow based on the internal servers’ configurations based upon the client’s needs. To allow a request to pass through a private network that has a firewall and is protected by a proxy server, it is necessary to traverse a proxy server that does not follow any of the local policies that govern the network. It is through reverse proxies that these types of requests from clients are completed. As a result, it is also possible to restrict clients’ access to the confidential data stored on the particular server to ensure that the data is kept confidential.
6. Forward Proxy
The most common use of forwarding proxies on the web is that it boosts internal network security by filtering internal/external data exchange between ‘clients’ and ‘target sites.’ A virtual private network (VPN) is typically used to provide a secure connection between a ‘sheltered’ network and a firewall (which determines whether a request should pass through or not) to transfer requests from one to the other.
7. SSL Proxy
SSL proxies are transparent servers that encrypt/decrypt traffic between clients and servers. Client/server ciphers and advanced/strong security protocols can be implemented with SSL proxies to obtain granular application information.
Following image shows exactly how SSL proxies work:
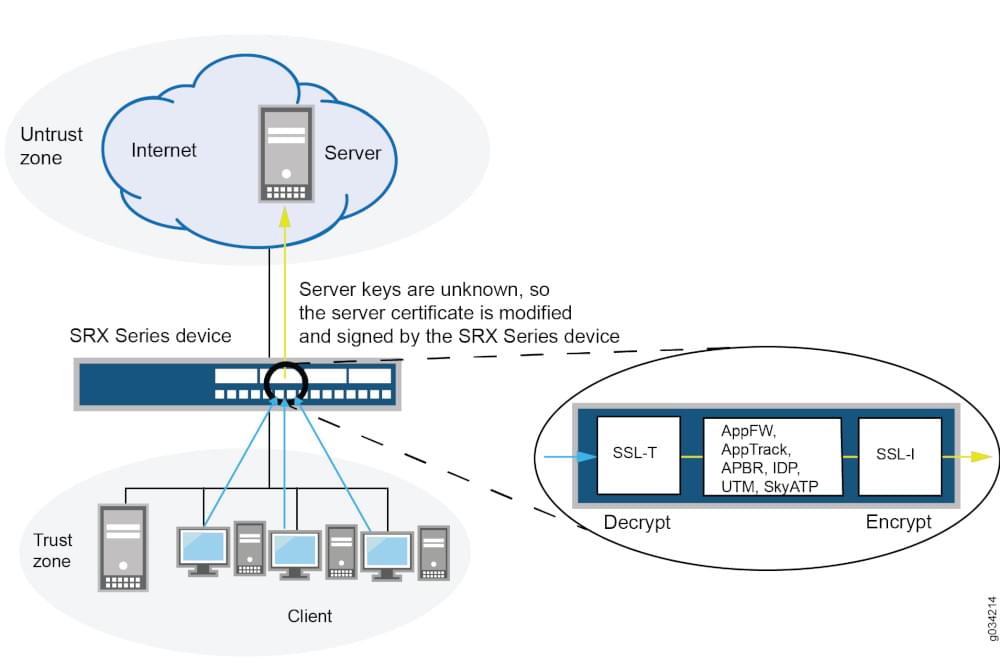
It provides cloud based web proxy security with a better understanding of potential threats that may be embedded in SSL encrypted traffic that was previously unknown to them.
8. DNS Proxy
A DNS proxy is a technology that takes requests in the form of DNS queries and forwards them to the domain server, where they can also be cached, and the flow of requests can be redirected.
9. Web Proxy Server
When a web proxy server forwards HTTP requests, only a URL is passed instead of a path. These servers respond to requests sent to them. Examples include Apache and HAP servers.
10. CGI Proxy
Developed a CGI proxy server to make websites more accessible. After accepting requests to target URLs using a web form, it will process the request, and once the result has been processed, it will be returned to the web browser.
Even though it is less popular because of some privacy policies like VPNs, it still receives a large number of requests also. Due to excessive traffic that can damage an organization’s website after passing the local filter, its usage has been reduced.
11. Suffix Proxy
This type of proxy preserves no higher level of anonymity. To bypass web filters, it is used. Even though it is easy to use and can be easily implemented, it is less used because of the many web filters it contains.
12. Distorting Proxy
It is preferred for proxy servers to generate an incorrect original IP address of their clients once they have been detected as a proxy server. HTTP headers are used to maintain the confidentiality of the IP address of the client.
13. Tor Onion Proxy
The purpose of this server is to provide online anonymity to the user regarding their personal information. It is used to route the traffic through various networks that are present around the world to make it difficult to track the user’s address and to prevent attacks on any anonymous activities that are taking place.
Anyone looking for the original address may find it challenging to do so, making it difficult for them to find it. A multi-fold encryption layer is used in this routing type. To prevent the information from being scrambled, each layer of the protocol is decrypted at the destination to receive the original content.
14. I2P Anonymous Proxy
As a result of the use of encryption, all the communications are hidden at various levels. In this way, I2P is a fully distributed proxy since the encrypted data is relayed between various network routers located at various locations. Besides being free of charge and open source, this software also resists censorship.
15. Anonymous Proxy
Proxy providers that provide anonymous proxy services are typically used by web servers that do not reveal the identities of their clients to their destination servers. The anonymizers, as they are commonly called, conceal the origin IP address, enabling geo/IP-based blocks as well as misrepresenting target data.
Using them can also prevent your competition from customizing their marketing materials or search results according to your IP address’s browsing history. This enables companies to get an objective view of the internet and prevent things like cookies or other identifiers from impacting the information gathered.
16. Highly Anonymity Proxy
The type of proxies prevents the original IP address from being detected and the fact that it is acting as a proxy server.
How Do You Connect To A Proxy Server?
To connect to a proxy server, while you need to:
- Set up a systems to initiate crawl jobs
- Install an integrated development environment like Visual Studio Code or Atom
- Select a programming language you feel easy with
- Go to the Smart Proxy docs and paste the snippet of code in your desired programming language
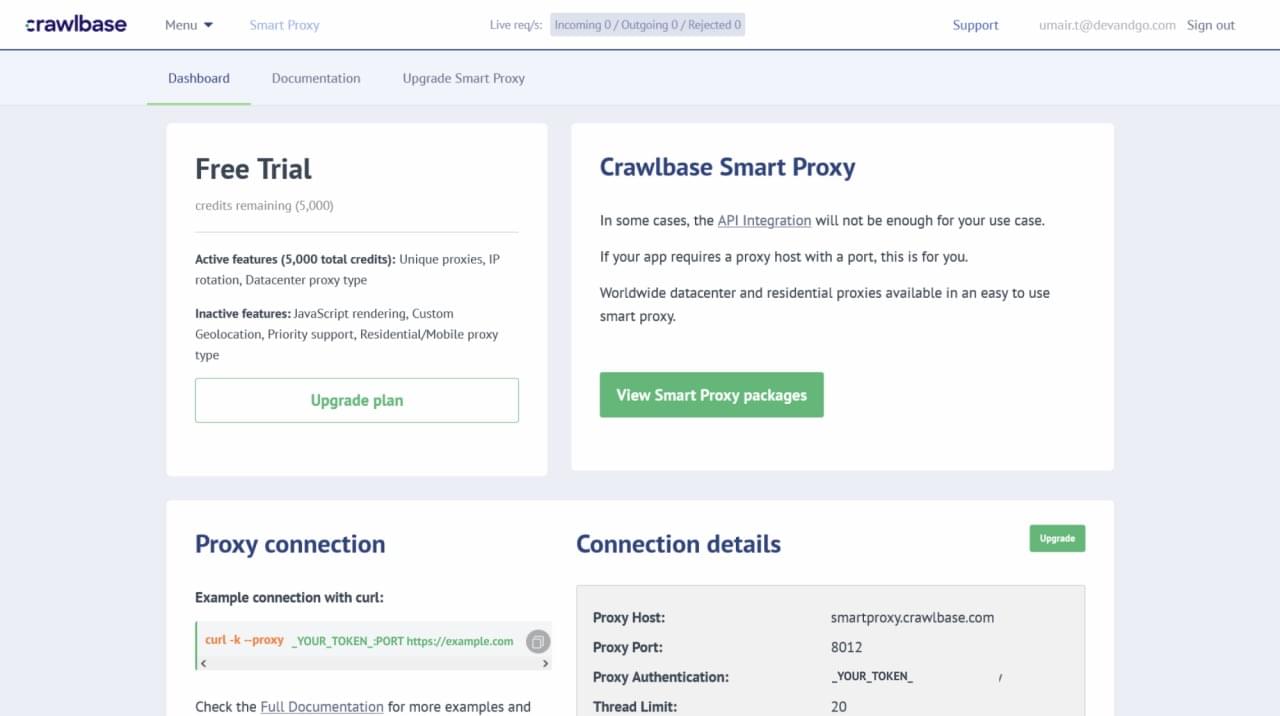
Copy-paste your token
Paste your link to scrape from
Run the code
We will you connect you to one of the Crawlbase for best results guaranteed. You don’t need to be a network engineer to do this job. Our engineers at the back-end handle and manage this for you round the clock.
How Does The Proxy Server Works Step By Step?
As mentioned above, a proxy server has an IP address that is assigned to it, and it serves as a gateway between the client and the Internet, functioning as a gateway. There is an IP address associated with the proxy server. A client’s computer knows this IP address as it is stored in its registry. Clients send internet requests that are redirected to the proxy.
Following that, the proxy server will fetch the response from the targeted server or site and forward the data from that page to the client’s internet browser (Chrome, Safari, etc.) as soon as the proxy server receives the response from the destination server.
- Requests from the internal host for a website to be processed
- Requests are routed through the proxy server. Using a rule-based approach, it analyzes the header and packet content by the rules
- An IP address from a different source is used to reconstruct the data packet by the server
- By transmitting the packet to a proxy server, the actual end user who made the request cannot be identified
- A returned packet is again sent to the proxy server to be checked against the rule base if it is returned
- Upon receipt of the packet, the proxy server reconstructs the packet and sends it to the source computer
Proxy servers access targeted sites on behalf of clients, collect information, and forward it to them. There is a clear illustration of how the proxy server works.
How To Configure Proxy Server by Crawlbase Smart Proxy API
1 | import requests |

Benefits of Using a Proxy Server
Several benefits can be gained from using proxy servers for businesses that can give them a competitive edge. As a result, they can be used as a firewall between the system and the internet, helping to keep hackers away from the system. The use of these technologies can also provide a means to collect IP-specific data, as well as provide users with access to regionally-specific content.
Businesses can perform functions in more than one location by defining a proxy server with an address associated with another country (for example, it may be possible to manage multiple eCommerce stores using a local IP address, or it may be possible to collect Google search trends specific to a particular city). It can prove to be a valuable tool to companies looking to reach new markets and audiences and to companies operating in multiple markets that want to expand their reach.
To simplify, here are some key benefits:
1. Enhanced security
It is possible to improve the security of the company’s network by using IP addresses that are not currently associated with the company using a proxy server.
If the IP address is easily accessible, passwords and different architectures can be used to protect organizations’ data from malicious use. However, it is still possible for this information to be hacked. To prevent such misuse of data, proxy servers are set up so that it is not possible for tracking IP addresses to be performed on data.
2. Improved performance
A proxy server can improve your website and overal network performance through caching web pages and files to enable bandwidth savings.
3. A higher level of security
A company can protect itself against attacks that can cause Denial-of-Service (DDoS).
4. Traffic monitoring
It is possible to filter traffic using a proxy server.
5. Collecting data
Companies can gain access to accurate information from a user/geo-location perspective. For example, you should do so if you need to obtain the correct pricing for a competitor’s product that is being sold in San Diego.
6. Content Filtering
Proxy servers ensure that the data accessed frequently on the website is retrieved very quickly by caching the website’s content.
7. Detailed analysis of packet headers and payloads
It is possible to track and restrict the packet headers and payloads of the requests made by the user nodes to access social websites on the internal server.
8. Controlling internet usage of employees and children
Proxy servers are used in this case to control and monitor how their employees and children use the Internet on the company’s network. Organizations commonly use it to deny access to a specific website while instead redirecting you with a nice note asking you to refrain from looking at any of the sites on the network.
Risks Associated with Proxy Servers
Proxy risks is one of the main concerns while opting a proxy for data collection. Free proxies do not make much investment in the back-end hardware or encryption. As a consequence, it will have a negative impact on performance and may even result in security issues.
1. Unauthorized Data Storage
Unreliable proxy servers may store your original IP address and your web request information in an unencrypted form and save it locally. You should always check if your proxy server saves and logs that data - and what policies they follow regarding data retention and law enforcement cooperation.
2. No encryption
If you do not use encryption, you should know that your requests will be sent in plain text. It will be possible for anyone to get access to usernames, passwords, and account information easily and quickly. You must ensure that whenever you use a proxy, it provides full encryption.
How Do You Find Your Proxy IP Address?
It might be necessary for you to find your proxy server address if you need to troubleshoot a networking problem or if you need to write down the address to configure a new device on your network. This information can be obtained by accessing the network settings on your computer, checking your browser settings, or using an online tool to detect proxy servers.
- Make sure the settings on your operating system are correct
- Make sure your computer’s browser is configured correctly
- Detect proxy server addresses with proxy server address detectors
Can Someone Fake Your IP Address?
Your IP address is one of the most important aspects of sending and receiving information online. A hacker, however, can use your IP address to obtain your valuable information, such as your location and online identity, if they know your IP address. If they were to use this information as a starting point, they might be able to hack your device, steal your identity, and do other things.
Make Scalable Connections Through Smart Proxy
Whether you are an individual user or a business owner, you must be aware of the various cyber threats that may threaten your business and operating system.
Proxy servers are needed for the job when you want to have true control over your internet privacy and security. With fast servers located all over the world, no matter where you are, you can access the content you want, no matter where you are. Your IP address and internet activities will be hidden under the Crawlbase anonymous proxy. You will be protected on any network, even using an unsecured public network.
Frequently Asked Questions (FAQs)
How does a proxy server differ from a packet-filtering firewall?
Proxy Server:
- Acts as an intermediary between a user and the internet, forwarding requests and responses.
- Can cache data, filter content, and anonymize internet usage.
- Operates at the application layer of the OSI model, understanding protocols like HTTP, FTP, etc.
Packet-Filtering Firewall:
- Controls network access by monitoring and filtering packets based on IP addresses, port numbers, and protocols.
- Operates at the network and transport layers of the OSI model.
- Does not analyze the actual content of requests like a proxy does.
Key Difference: A proxy focuses on content-level tasks (e.g., caching, content filtering), while a packet-filtering firewall focuses on allowing or blocking packets based on set rules.
What is a proxy server address?
A proxy server address is the IP address or hostname of a proxy server, often accompanied by a port number. It acts as the entry point for client devices to connect to the proxy server for relaying their requests to the internet.
Example: 192.168.1.1:8080
Here, 192.168.1.1 is the IP address, and 8080 is the port number.
How to find a proxy server address?
To find the proxy server address being used by your device or network:
Windows:
- Go to Settings > Network & Internet > Proxy.
- Check if “Use a proxy server” is enabled.
- The address and port will be displayed there.
MacOS:
- Go to System Preferences > Network.
- Select the active network and click Advanced.
- Navigate to the Proxies tab to find the proxy details.
Browser Settings:
- For browsers like Chrome or Firefox:
- Open settings and search for proxy.
- It will display or link to system proxy settings.
Command Line (Windows):
Run the command:
netsh winhttp show proxy
What is a common function of a proxy server?
A common function of a proxy server is to act as a gateway between users and the internet, providing features such as:
- Content Caching: Speeds up access by storing frequently requested content.
- Anonymity: Hides the user’s IP address to protect their identity.
- Content Filtering: Blocks specific websites or content based on predefined rules.
- Access Control: Limits access to the internet or specific resources based on user credentials or policies.