Gateways bridge local networks and large-scale networks, such as the Internet. Proxy servers intercept connections between senders (clients) and receivers (servers). Receiving the data on an incoming port and forwarding it to the rest of the network on an outgoing port.
You can encrypt your data. This makes it impossible to read in transit. It can also block access to specific web pages based on your internet protocol address if you use a proxy server. A proxy server forwards traffic. It also hides a server’s IP address for security by rotating IPs. Additionally, using caching mechanisms to improve performance by storing requested resources.
This article will focus on a specific proxy type, SOCKS5. This will help you understand the basic principles of proxy connections.
What is a SOCKS5 Proxy?
SOCKS is a proxy server. It connects to servers behind firewalls for clients. It exchanges network packets between them. Their network has limitations. These cause direct inaccessibility. So, clients use SOCKS proxy servers behind firewalls. So, it causes delays in TCP and UDP sessions. These delays occur over firewalls between SOCKS proxy servers and their users.
Because SOCKS is a layer 5 protocol, a SOCKS tunnel cannot tunnel protocols below that level. Layer 5 functionality can prevent attackers from using tools to scan. They use them to scan half-open connections, such as ARP and ping, which are two examples of these.
Due to its position between SSL (layer 7) and TCP/UDP (layer 4), it can handle HTTP, HTTPS, POP3, SMTP, and FTP requests. SOCKS can do many tasks. These include email, web browsing, file transfers, and sharing. Besides HTTP proxies proxies. Proxies often interpret and forward HTTP or HTTPS traffic. They do so between clients and servers.
Difference Between SOCKS4 & SOCKS5 Proxies
There are two versions of SOCKS; SOCKS4 and SOCKS5. They are similar, but SOCK5 supports many authentication methods. SOCKS4 does not support any. Also, SOCK5 has better security. But, SOCKS4 does not support UDP proxies. SSH tunneling with SOCK5 creates a secure connection with authentication.
How Does SOCKS Proxy work?
A SOCKS proxy routes web traffic through a server. It does this to hide the client’s internal protocol address and encrypt the data. In web scraping and crawling, SOCKS proxies hide the IP address of the scraping machine. They also bypass geo-restrictions and avoid IP bans.
How Does a SOCKS5 Proxy Work?
Proxy servers route traffic through arbitrary IP addresses before reaching destination sites. In technical terms, SOCKS5 creates UDP or TCP connections through proxy servers. It connects to servers based on arbitrary IP addresses. This protects the users’ identity by hiding its location.
If your IP address is 1.1.1.1, SOCKS proxy traffic will appear to the website from 2.2.2.2. Your original IP address will not be visible on the website. While this hides your location, it doesn’t guarantee the security of your traffic. The traffic you send through proxies is not encrypted like VPNs - anyone can watch what you’re doing.
Read More on: Proxies vs VPNs
No SOCKS5 proxy server is 100% anonymous. Getting close to privacy requires being aware of how you use the Internet. It means knowing what services and security tools you use. But, a proxy provider, VPN, or encrypted app will not let you stay anonymous.
Does SOCKS5 Hide Your IP?
Proxy servers route traffic through arbitrary IP addresses before reaching destination sites. SOCKS5 creates UDP or TCP connections. It uses proxy servers with arbitrary IP addresses. This protects the user’s identity by hiding its location.
A SOCKS proxy does not make a full TCP connection. It does not need authentication. A SOCKS5 proxy uses an encrypted tunneling method. It, for example, uses Secure Shell (SSH). This provides a more secure connection.
Benefits of SOCKS5 Proxy
SOCKS5 Proxy has the following benefits that make it a good choice:
1. Firewall-protected backend services access
To lower security risks, we host clusters in the cloud. They are behind a firewall. Both methods have their limits. They struggle to access backend services in a cluster.
- It is possible to expose backend services to the public. This has security risks.
- To allow traffic to backend services, whitelist the client or user’s IP address. This is not the best solution for changing IP addresses, though.
A SOCKS5 proxy has dynamic port forwarding. It would be better than the two bad options above. Administrators or developers can access backend services in a cloud cluster. They do this through a public network. They can do this to debug, check, and manage the cluster. They can do it without exposing the backend service ports.
Bastion hosts limit their access to the outside world. They allow you to access remote VPC instances. For example, suppose you work with a virtual private cloud (VPC). A SOCKS5 proxy can be set up to enable SSH dynamic port forwarding (to access the remote instances in the VPC). The bastion host is accessible via port 22 (SSH).
2. Improved performance on P2P platforms
The SOCKS5 protocol is faster than other proxies. Its data packets are smaller than those sent by other proxy servers. It allows users to access P2P sharing websites faster. This is because it provides faster download speeds.
3. Fast and reliable connection
SSH tunneling sends all TCP and UDP traffic through SOCKS5 proxies. The proxies route the traffic to the correct services. There is no need for layer 7 application proxies for each service.
4. No need for a special setup
You need SSH access to the Edge node or cluster gateway. SOCKS5 does not need setup. Admins and developers do not need a VPN. They use it to access resources behind the firewall.
5. Don’t use public or free proxy servers
Through SSH tunneling. SOCKS5 proxies route all TCP and UDP traffic to their services. There is no need for layer 7 application proxies for each service.
6. Error-free performance improvements
SOCKS5 doesn’t rewrite data packets like other application proxies. Traffic relays between devices. Because of this, performance increases naturally, and errors are less likely to occur.
7. Increased reliability and speed
A SOCKS5 proxy server can use UDP protocol, unlike its predecessors, which only use TCP. TCP ensures packets arrive from one end to the other. It establishes a connection between a client and a server. Fixing the format of the content is essential to making it easy to transfer.
Unlike TCP, UDP never converts data packets into fixed packets. UDP does not care whether packets from the client or the servers reach the other side. It does not require them to arrive in the same order. Thus, SOCKS5 can provide faster speeds and reliability with these UDPs.
How to Setup SOCKS5?
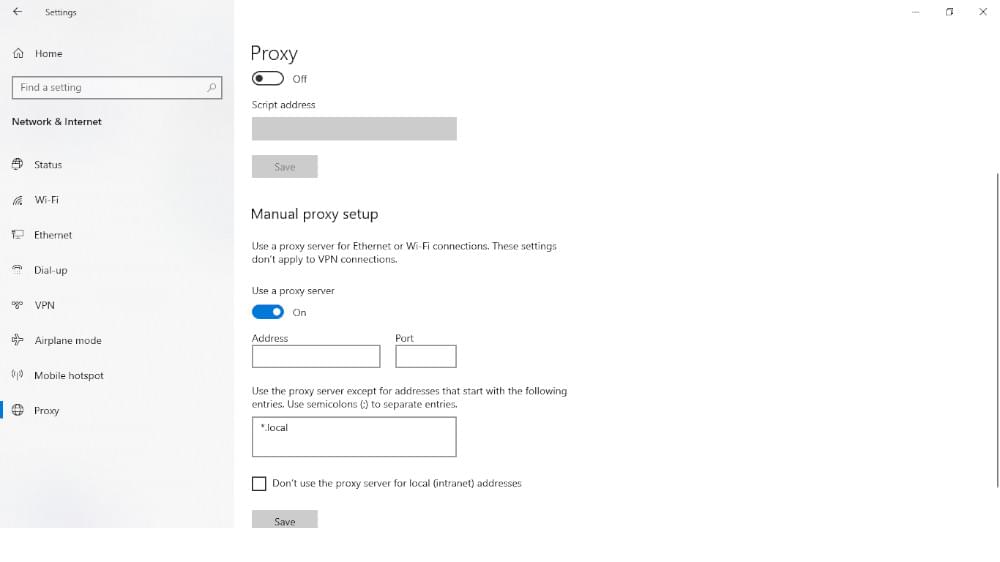
To SOCKSify an IT environment, the client side needs an app that can support SOCKS5.
- Go to Control Panel > Internet Options.
- Navigate to the Connections tab.
- Then click on LAN settings.
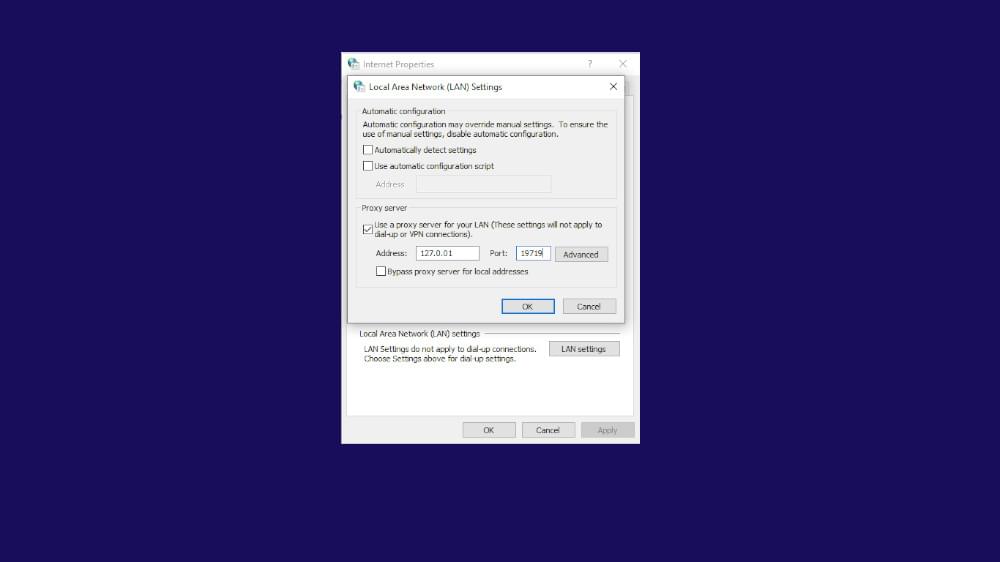
- Then enable Use a proxy server for your LAN.
- Activate the bypass proxy server for local addresses.
- Then click Advanced.
- Disable Use the same proxy server for all protocols.
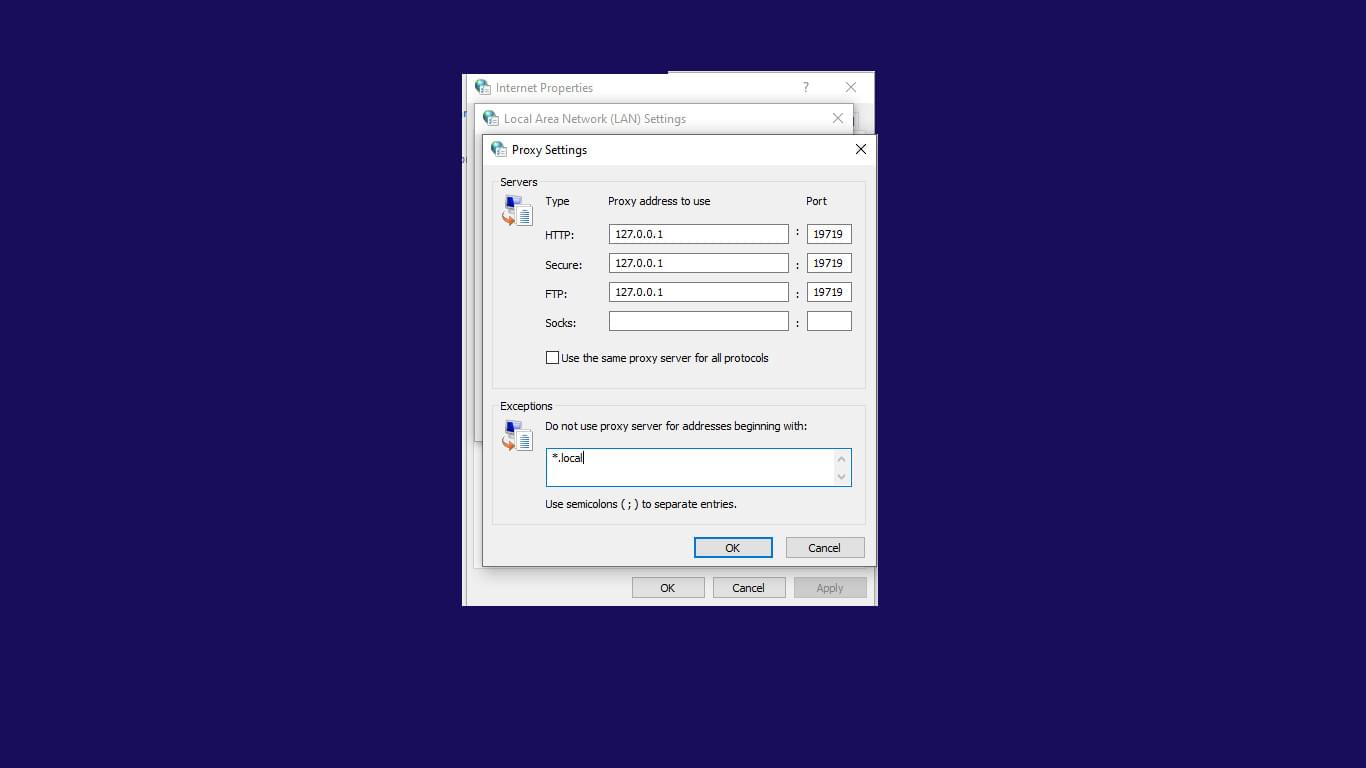
- At SOCKS, specify the SOCKS proxy’s server address and port.
- Delete all data at HTTP, Secure, and FTP.
- Then click OK > Apply.
If you have Windows 10, you can configure the SOCKS 5 proxy settings. You can do this without installing extra software. The setup works with all internet software. So, you don’t need to use your web browser with the setup.
Should You Use SOCKS5 with a VPN?
Whether you should use SOCKS5 with a VPN depends on your specific use case and what you are trying to achieve.
You can activate SOCKS proxies and VPNs on your computer. Turning them on and off is easy, depending on what you want to do with them. Others use both to add an extra layer of security and anonymity, but this is optional. Adding extra security to SOCKS proxies or VPNs is optional. They are secure on their own.
However, if your main goal is to access geo-restricted content, using a VPN alone may be sufficient. Also, using a SOCKS5 proxy with a VPN can slow your internet connection. So, it’s better not to use them together.
It is wise to consider your needs and wants before deciding.
Is SOCKS5 the Same as VPN?
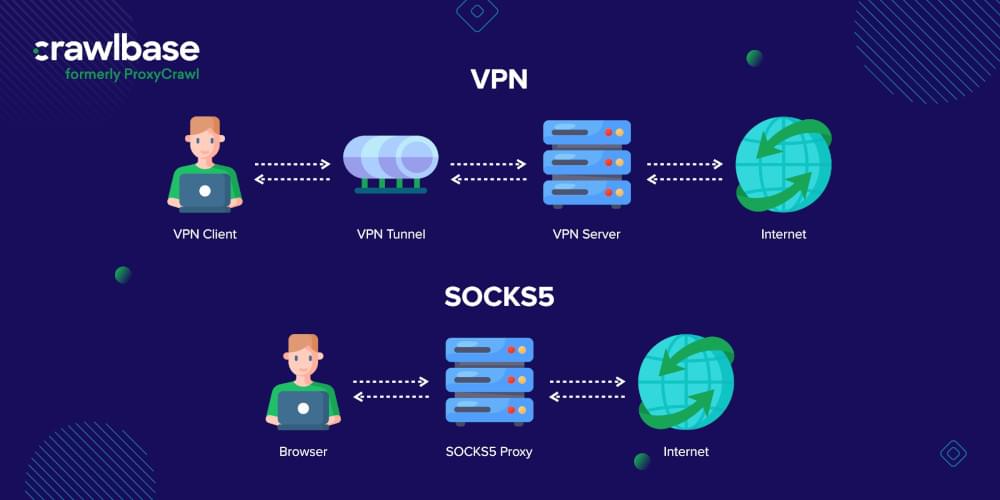
SOCKS5 proxies and VPNs give anonymous web browsing. However, VPNs do this differently than SOCKS proxies. With a VPN, you can connect directly to the other website’s server. This is instead of just connecting to the network you’re trying to access.
A VPN encrypts your traffic, whereas proxies do not. A VPN is more likely to stay stable. Proxies tend to drop more often. This makes them slower.
As VPNs encrypt and scramble all data sent over WiFi networks, tracking your data when you use them is almost impossible. You can also use a VPN to bypass firewalls and geolocation restrictions, just like you can do with a SOCKS proxy. There are several differences between the two options, and a simple discussion can help you decide which is best for you.
A SOCKS5 proxy is useful if: you want to boost your online anonymity and also to get fast browsing speeds.
You should use a VPN if: When it comes to protecting your online privacy, encryption is the best way.
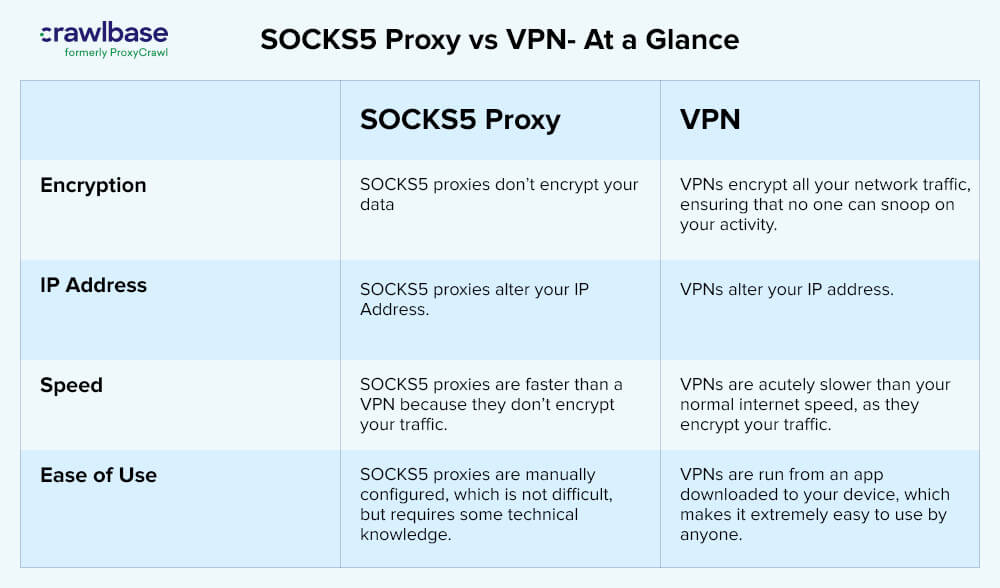
Check out the following comparison table if you want to learn more about SOCKS5 proxies and VPNs.
Final Thoughts
The SOCKS5 proxy is light and general purpose. It sits at layer 4 (the transport layer) of the OSI model. It tunnels out network traffic with an in-between method. The product supports many types of traffic. Different protocols, such as HTTP, SMTP, and FTP, generate them. It can also work with any IP-based protocol. Compared to a VPN, SOCKS5 is much faster and easier to use than a VPN. Through SOCKS5, cloud users can access resources behind the firewall. They do this through a secure tunnel, like SSH, as the proxy uses tunneling.
Smart Proxy is a very advanced proxy service. It offers a unique mix of features. These give users an unparalleled experience. It uses various anti-blocking techniques and anti-captcha solutions. This makes it one of the market’s most strong and reliable proxies. Also, it has unlimited bandwidth. It has custom geolocalization and integrates artificial intelligence. These provide users with unmatched speed, control, and intelligence. Smart Proxy is a must-have for anyone in need of a premium proxy solution that too with a cloud proxy solution.