APIs (Application Programming Interfaces) might sound complex, yet they power our daily digital interactions. You’re using APIs when you check weather updates, send social media messages, or make online payments - without even realizing it.
Understanding APIs and their functions can seem daunting initially. This article will help you learn the API definition and fundamental concepts clearly. Business owners curious about API capabilities and developers starting their tech careers will find everything they need here. Crawlbase APIs are beginner-friendly, with simple endpoints to start automating your scraping tasks today. Sign up now
Want to understand APIs better and see how they can enhance your digital projects? Let’s take a closer look!
The Business Value of APIs
The digital economy has transformed APIs from basic technical tools into valuable business assets. These digital bridges now create real value for organizations worldwide.
Expanding Market Reach
APIs are reshaping how businesses grow their market presence. Recent studies show that nearly two-thirds of companies generate revenue through APIs. The numbers tell an interesting story - 43% of businesses report that APIs bring in over a quarter of their revenue. Opening up systems through APIs lets companies reach new markets and build strategic collaborations that were previously impossible.
APIs help expand market reach in several ways:
- Smooth integration with partner ecosystems
- New distribution channels
- Access to untapped customer segments
- Developer communities that promote innovation
Businesses now monetize their digital assets through APIs in innovative ways. API solution has grown beyond technical roots to become a revenue generator. Companies transform their existing data and services into profitable streams through various API monetization models.
For instance, weather services monetize immediate data through APIs and sell it to agriculture, logistics, and event planning industries. Financial institutions also create new income by offering premium APIs for advanced market analytics and high-frequency trading.
Improving Customer Experience
APIs reshape how businesses connect with their customers. Today’s consumers want personalized, immediate experiences across every channel. APIs make this possible.
Streaming sites use this approach perfectly - they utilize APIs to track listening habits and create personalized playlists that adapt to the time of day and activity. This personalization is a crucial differentiator in today’s market.
An API-first strategy breaks down data silos to create a unified customer view. Companies can deliver consistent experiences across mobile apps, social media, and AI-powered chatbots.
Essential API Architecture Concepts
Let’s tuck into the building blocks that make APIs work. These core concepts will help you learn how APIs enable the business values we discussed earlier.
Request-Response Model
APIs manage conversations between two systems. Picture ordering at a restaurant - you (the client) request the waiter (the API), and they bring back your order (the response). This request-response model creates the foundations of how APIs work.
API Endpoints Explained
Digital doorways enable these conversations through API endpoints. These specific addresses allow our API connections. Here are the common endpoint types we use:
- Resource Endpoints: Access specific data (like user profiles)
- Action Endpoints: Perform specific operations (like processing payments)
- Collection Endpoints: Handle groups of resources (like lists of products)
- Search Endpoints: Enable data queries and filtering
Authentication Basics
Security matters just like we wouldn’t let strangers into our house without identification. Authentication acts as our security guard and verifies who makes the request. Different authentication methods serve various needs:

Authentication implementation requires a balance between security and user experience. To name just one example, see OAuth 2.0 - it provides excellent security but might be excessive for simple internal applications where basic API keys would work better.
These concepts create magic when they work together. Each request to an endpoint includes authentication credentials, and the API returns the needed data - all following our request-response pattern.
Note that these concepts are the foundations of any API software implementation, from simple weather apps to complex enterprise systems.
Common API Communication Styles
API communication styles come in three distinct flavors. Each serves a unique purpose in modern software architecture. Let’s see how these approaches help us build better-connected systems.
REST APIs Basics
REST (Representational State Transfer) stands at the vanguard of modern API standards. This style has become accessible to more people and makes server-side data available through simple formats like JSON and XML. REST’s appeal comes from its stateless nature. Each request contains all the information needed, which makes it perfect for web applications.
Key REST characteristics:
- Uniform interface across all platforms
- Client-server decoupling
- Built-in caching capabilities
- Flexible data format support
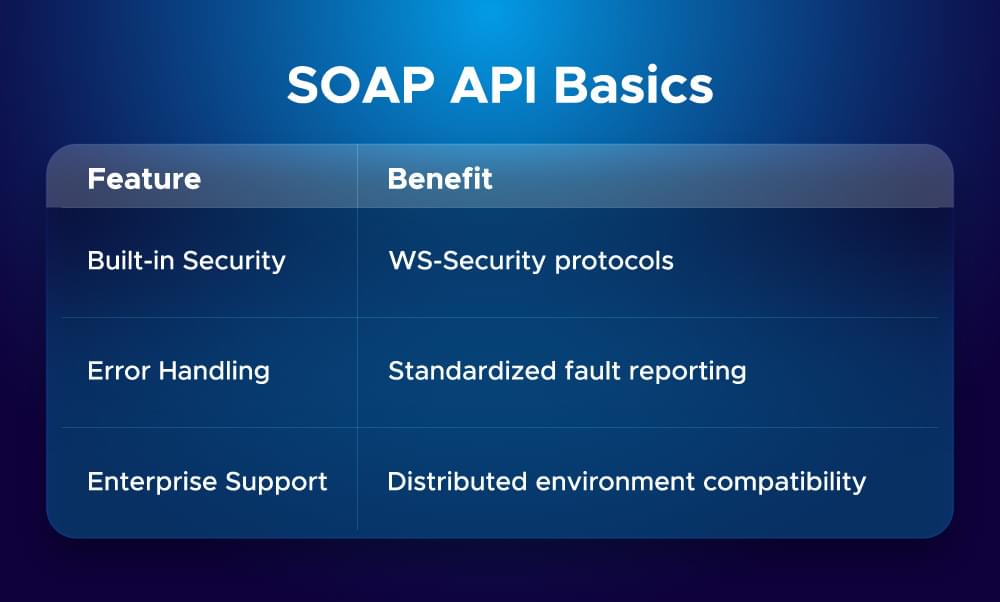
SOAP API Basics
SOAP (Simple Object Access Protocol) has become the preferred choice for enterprise-grade security and standardization. Unlike REST’s flexibility, SOAP enforces strict rules through its XML-based messaging framework. SOAP proves valuable, especially when you have:
Common Security Risks
API vulnerabilities show an alarming trend. Recent studies show that 90% of web applications face significant security risks through exposed APIs than through their user interfaces. These threats need our attention:
- Broken Authentication: Attackers exploiting weak authentication mechanisms
- Object Level Authorization: Unauthorized access to sensitive data
- Excessive Data Exposure: APIs returning more data than necessary
- Resource Management: Lack of rate limiting leading to DDoS attacks
Best Practices for Protection
Multiple layers of security protect APIs better. We encrypt all traffic using TLS (Transport Layer Security). This means intercepted communications remain unreadable to attackers.
OAuth 2.0 handles authentication for user-centric applications. It acts like a security guard who checks both ID and access permissions. Our security approach includes:
- Use an API gateway to centralize security controls
- Implement rate limiting to prevent abuse
- Confirm all input data to prevent injection attacks
- Monitor API usage patterns for suspicious activity
- Keep our API documentation up-to-date but restricted
A solid understanding of API security helps protect digital assets while keeping modern applications flexible and functional. Building trust with users and partners starts with strong security measures.
How to Choose the Right API Solution
The right API solution can determine the success of our digital initiatives. Security aspects form the foundation, and now we’ll take a closer look at making informed decisions about APIs that match our business goals.
Review the API requirements
Our API evaluation process focuses on three key requirement types:
- Functional Requirements: What the API needs to do
- Non-functional Requirements: How well it should perform
- Implementation Requirements: How it will be integrated
The review process includes availability, scalability, and performance. To cite an instance, real-time applications need APIs with response times under 90 milliseconds to deliver a smooth user experience.
Compare the various API options
A solid understanding of our requirements enables better comparison of API solutions. This framework helps us review options:
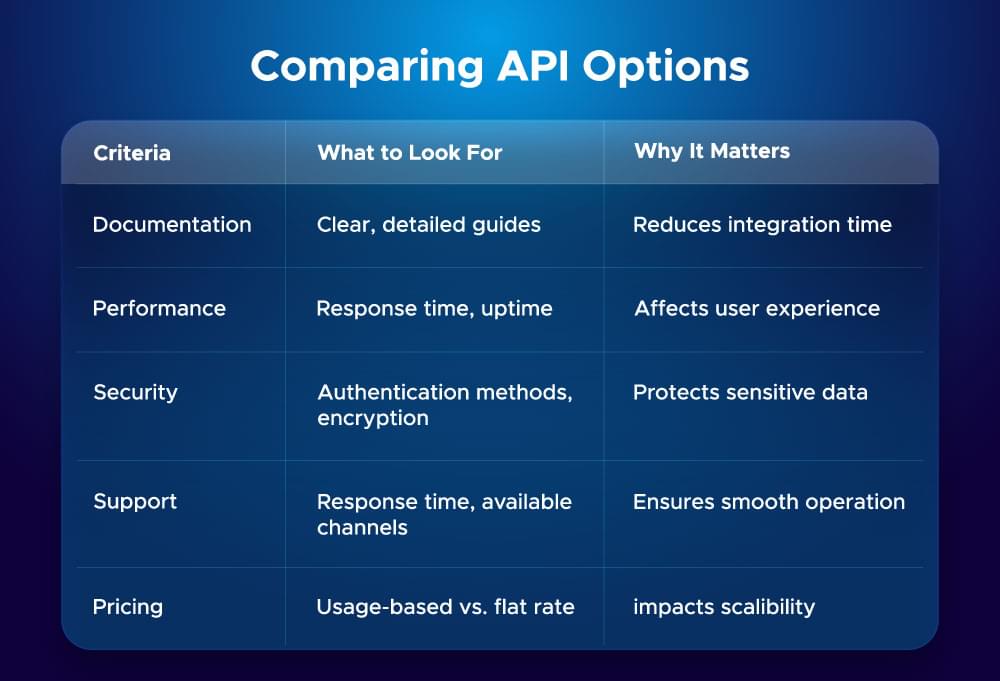
Detailed documentation serves as a roadmap for our integration experience. Our analysis of how APIs work with existing systems goes beyond simple functionality to understand the entire integration landscape.
Review the API integrations and compatibility
Long-term sustainability matters as much as technical compatibility. Here are some key factors to watch out for:
- Technical Alignment
- Programming language support
- SDK availability
- Development environment compatibility
- Operational Readiness
- Monitoring capabilities
- Error handling mechanisms
- Rate limiting policies
- Business Continuity
- Vendor stability
- Service level agreements
- Disaster recovery plans
Successful API integration requires more than just matching technical specifications. Our chosen API solution must align with our existing technology stack while offering scalability for future growth.
Business-critical applications demand reliable service from API providers. We evaluate them based on carrier-grade capabilities and SDK support across various programming languages, ensuring the solution can grow with our evolving needs.
Selecting an API provider is akin to choosing a long-term business partner. The provider’s track record, support quality, and capacity for growth are just as important as technical compatibility. A thorough evaluation of these factors helps lay a solid foundation for our digital initiatives.
Final Thoughts
Your path to successful API implementation starts with relying on user-friendly tools and strong security measures for your projects. When interacting with APIs for web scraping, you need a reliable solution to access and extract web data without getting blocked. Crawlbase’s Crawling API is a great option. It fetches the HTML content of any public web page, so you can focus on working with the data instead of managing infrastructure or headers.
Test Crawling API, your first 1000 requests are free of charge; Sign up now.
Frequently Asked Questions (FAQs)
Q1. What is an API, and how does it work?
An API (Application Programming Interface) is a set of protocols and tools that allow different software applications to communicate with each other. It acts as an intermediary, enabling one application to request and receive data or services from another. Think of it like a waiter in a restaurant, taking your order (request) to the kitchen (server) and bringing back your food (response).
Q2. How can I start learning about APIs?
To begin learning about APIs, start by understanding their basic concepts and functions. Familiarize yourself with popular terms like endpoints, requests, and responses. Explore online resources, tutorials, and documentation for popular APIs. Practice by working with simple, well-documented APIs, and gradually progress to more complex implementations as you gain confidence.
Q3. What are the different types of API communication styles?
The main API communication styles are REST (Representational State Transfer), SOAP (Simple Object Access Protocol), and GraphQL. REST is widely used for web services, SOAP is popular in enterprise environments, and GraphQL offers flexible data querying. Each style has its strengths and is suited for different use cases.
Q4. How important is security in API implementation?
Security is crucial in API implementation. It protects sensitive data, prevents unauthorized access, and maintains user trust. Key security measures include using API keys or tokens for authentication, implementing encryption (TLS), validating input data, and monitoring for suspicious activity. Regular security audits and updates are also essential to address evolving threats.
Q5. What should I consider when choosing an API solution?
When selecting an API solution, consider factors such as your specific requirements, the API’s documentation quality, performance metrics, security features, and support options. Evaluate how well it integrates with your existing systems, its scalability, and its pricing model. Also, consider the API provider’s reputation and long-term viability to ensure a sustainable solution for your needs.